Superhydrophobic Surface for Ice Mitigation: Mechanisms, Fabrication Strategies, and App...
DOI: 10.62762/JAMR.2025.980268
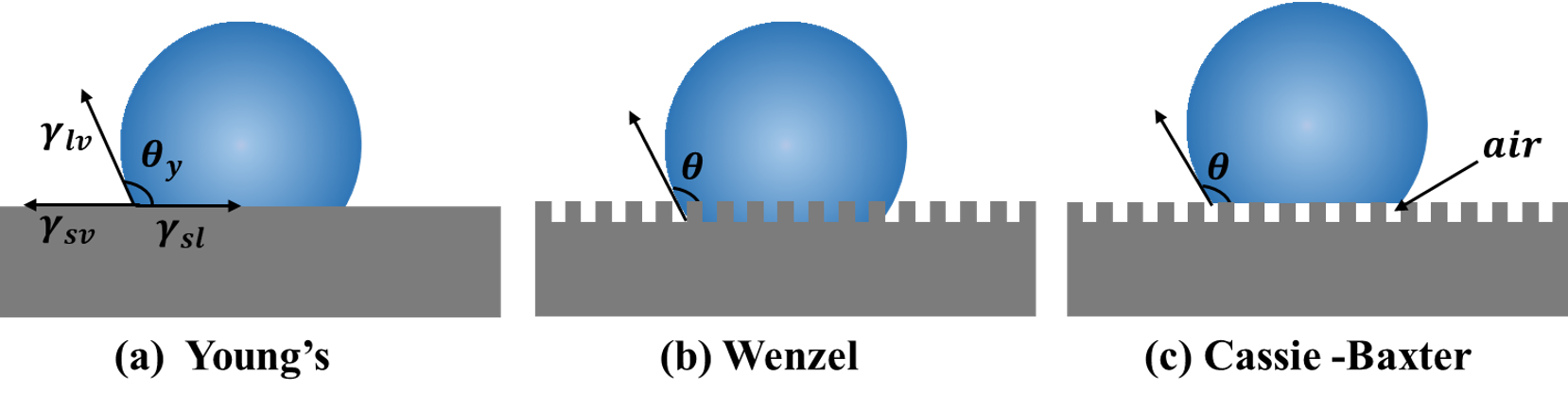
DOI: 10.62762/JAMR.2025.980268
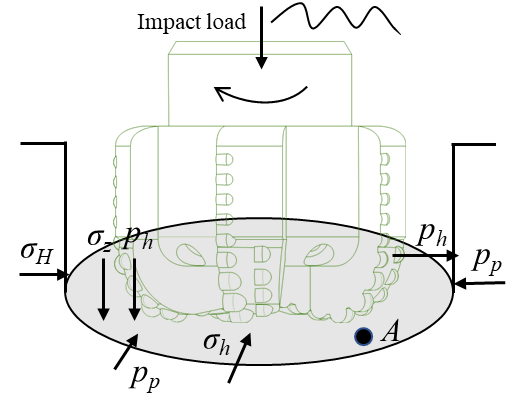
DOI: 10.62762/RS.2025.804345
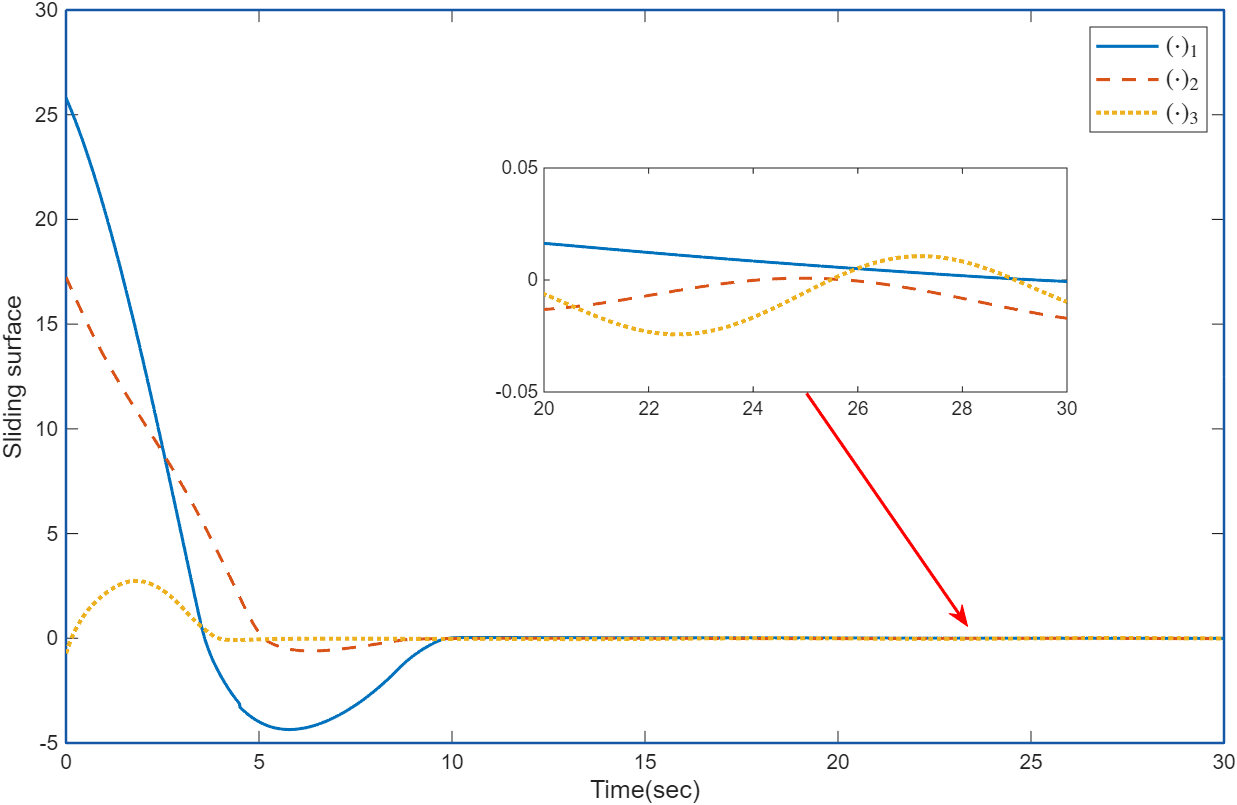
DOI: 10.62762/AEC.2025.182476
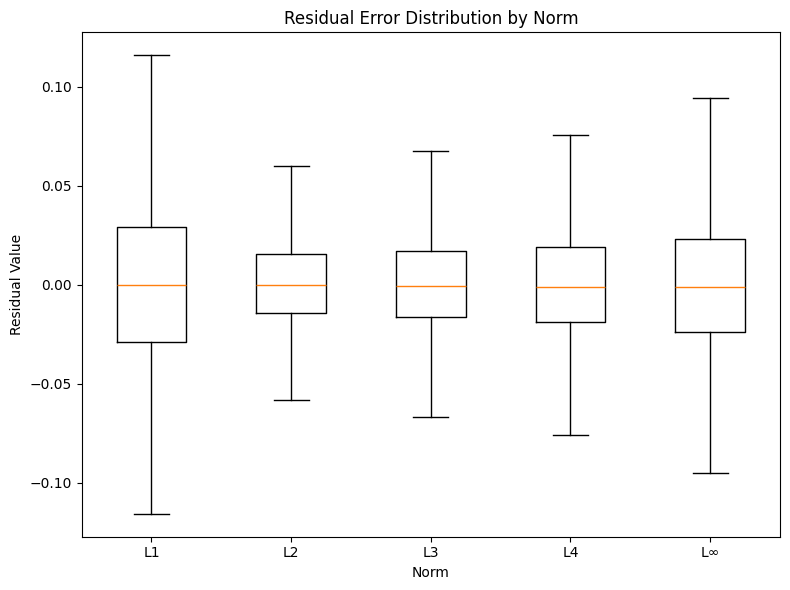
DOI: 10.62762/JIAP.2025.744487
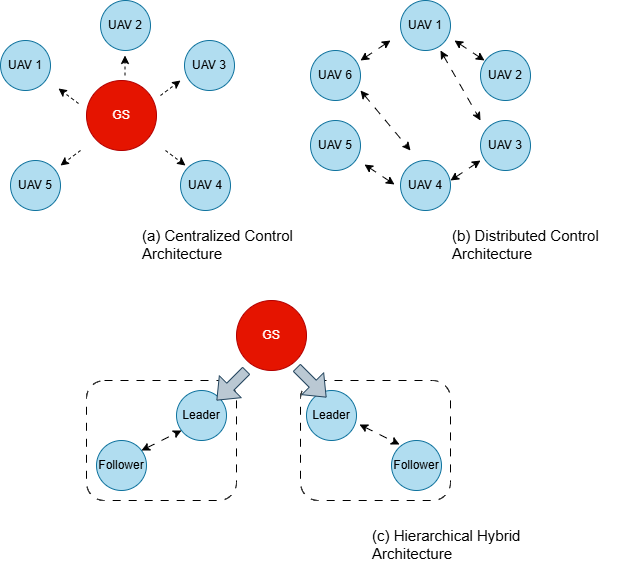
DOI: 10.62762/AEC.2025.339037
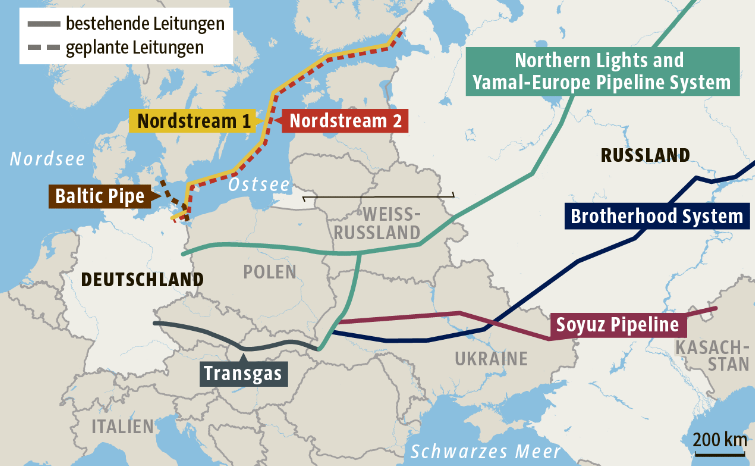
DOI: 10.62762/JGEE.2025.372522
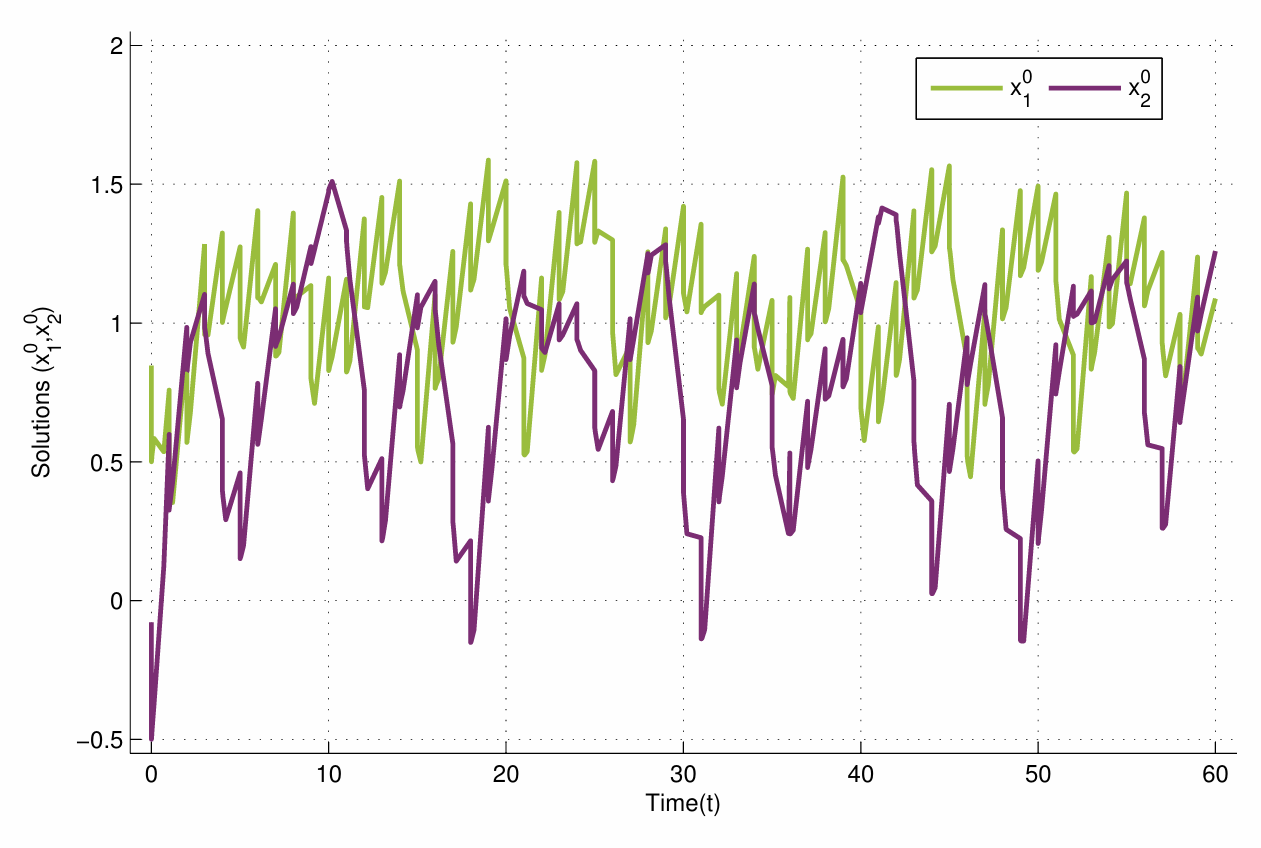
DOI: 10.62762/JNDA.2025.838385
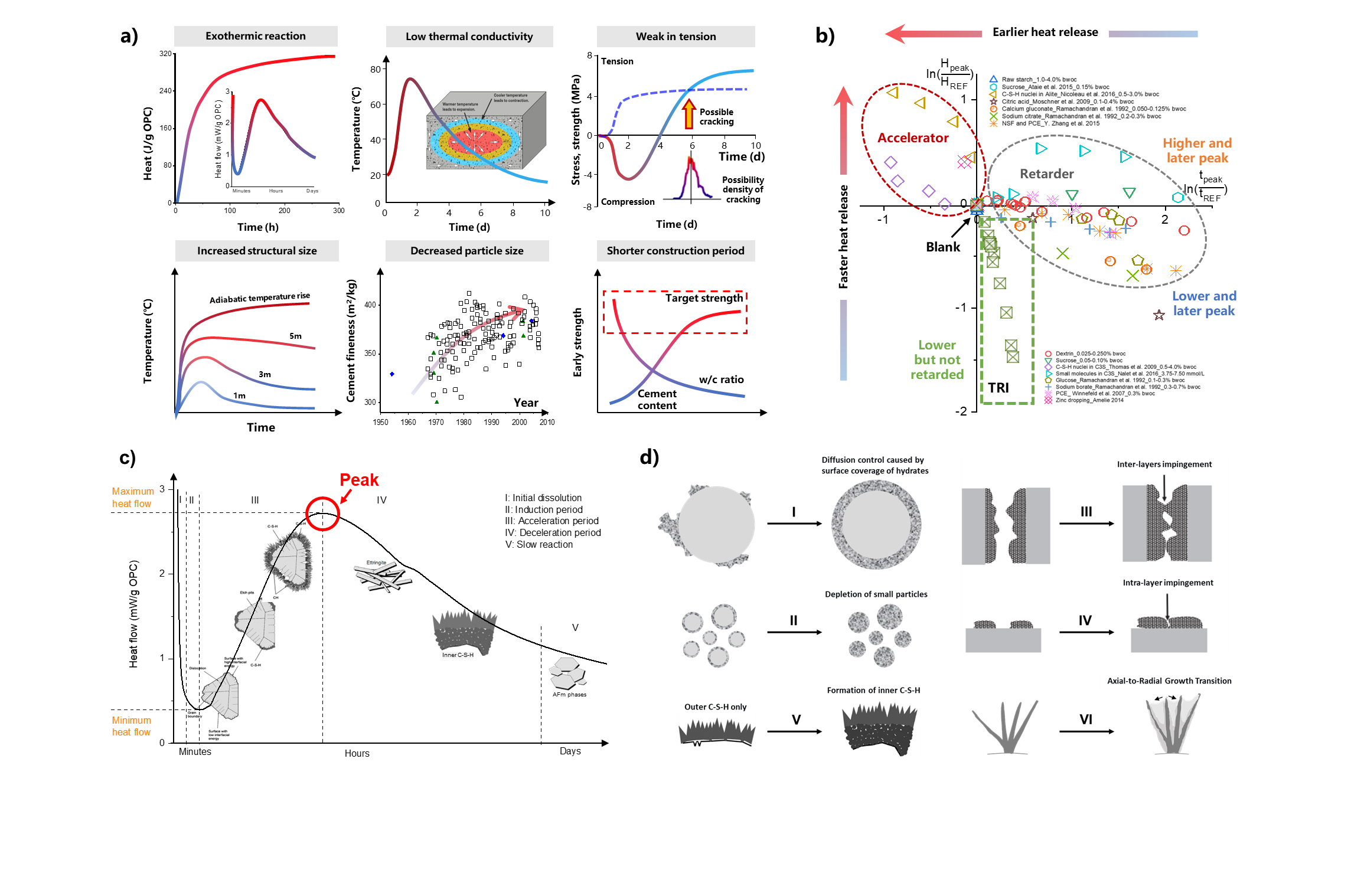
DOI: 10.62762/JAMR.2025.738370
DOI: 10.62762/JIAP.2025.569459
Explore our curated collections focusing on emerging research frontiers. Submit your work before the deadline!
Deadline: January 16, 2026
Journal: Chinese Journal of Information Fusion
Deadline: March 31, 2026
Journal: Sustainable Intelligent Infrastructure







